19 Firewalld Policy

The purpose of the Firewalld Policy is to apply firewalld rules to the client machine.
This policy is physically stored on the SYSVOL in the MACHINE/Registry.pol file within the subdirectory of the Group Policy Object. It is stored in registry format. See chapter 21 for details on how to manually modify this file.
19.1 Server Side Extension
The Server Side Extension (SSE) for the Firewalld Policy is distributed using Administrative Templates (ADMX). Refer to chapter 20.1 in section 20.1.1 for details about Administrative Templates.
Setting up the ADMX templates for this policy is described in chapter 22 section 22.1.
19.1.1 Managing Firewalld Policy via the GPME
Open the Group Policy Management Editor (GPME) and navigate to Computer Configuration > Policies > Administrative Templates > Samba > Unix Settings > Firewalld.
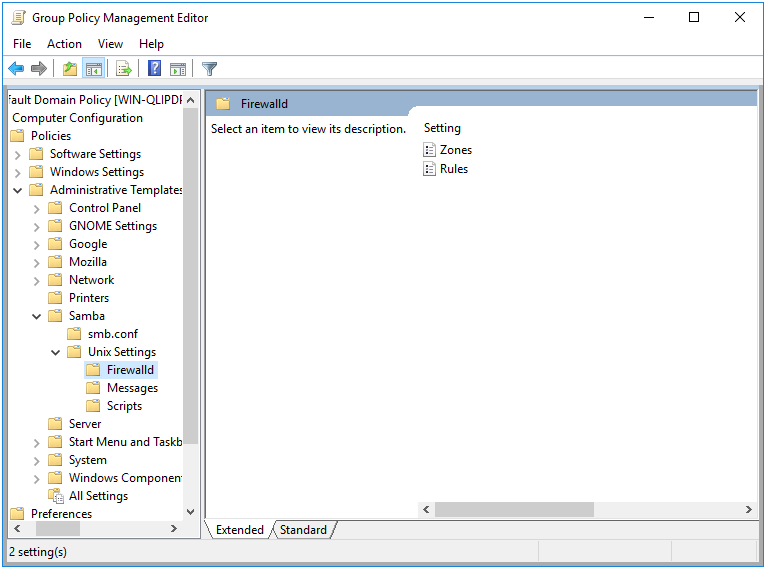
Figure 19.1: Group Policy Management Editor
You can see we have the options to create firewall rules, and firewall zones. For this example, we’re going to create a single rule in a new zone named “work”.
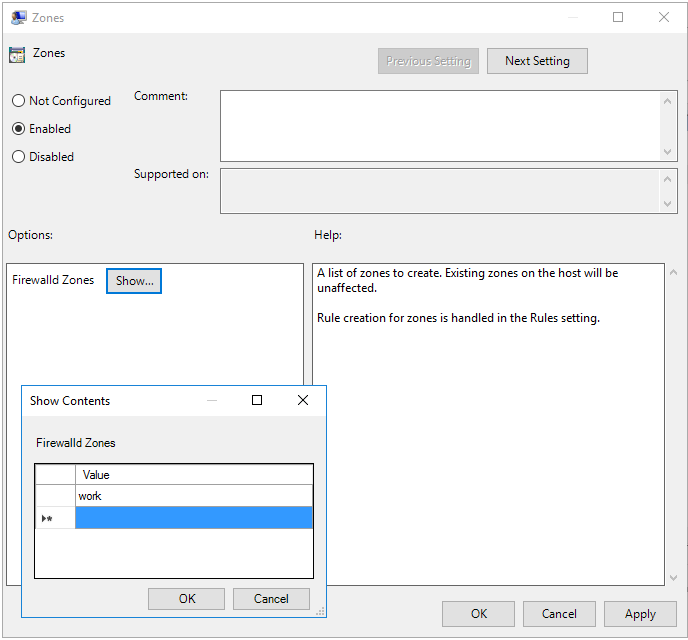
Figure 19.2: New Zone
We’ll define our new rule as follows.
{ "work":
[
{
"rule": { "family": "ipv4"},
"source address": "172.25.1.7",
"service name": "ftp",
"reject": {}
}
]
}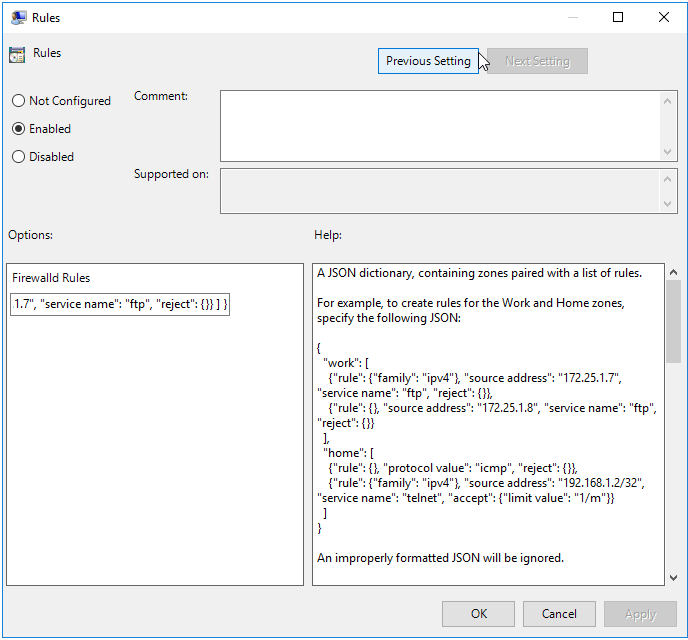
Figure 19.3: New Rule
19.1.1.1 Firewalld Policy Rule Definitions
The policy provides for the creation of rules and zones. Zones are defined as a list in the Zones setting in the Firewalld policy. Existing zones on the host will be unaffected.
Rules are defined using a JSON dictionary, containing zones paired with a list of rules.
For example, to create rules for the Work and Home zones, specify the following JSON:
{
"work": [
{
"rule": {"family": "ipv4"},
"source address": "172.25.1.7",
"service name": "ftp",
"reject": {}
},
{
"rule": {},
"source address": "172.25.1.8",
"service name": "ftp",
"reject": {}
}
],
"home": [
{
"rule": {},
"protocol value": "icmp",
"reject": {}
},
{
"rule": {"family": "ipv4"},
"source address": "192.168.1.2/32",
"service name": "telnet",
"accept": {"limit value": "1/m"}
}
]
}The rule structure loosely follows the Firewalld Rich Language Documentation. The general rule structure follows.
{
"rule": {
"family": "ipv4 | ipv6",
"priority": "priority"
},
"source [not] address | mac | ipset":
"address[/mask] | mac-address | ipset",
"destination [not] adress": "address[/mask]",
"service name": "service name",
"port": {
"port": "port value",
"protocol": "tcp | udp"
}
"protocol value": "protocol value",
"icmp-block name": "icmptype name",
"Masquerade": true|false,
"icmp-type": "icmptype name",
"forward-port": {
"port": "port value",
"protocol": "tcp | udp",
"to-port": "port value",
"to-addr": "address"
},
"source-port": {
"port": "port value",
"protocol": "tcp | udp"
},
"log": {
"prefix": "prefix text",
"level": "emerg | alert | crit | error
| warning | notice | info | debug",
"limit value": "rate/duration"
},
"audit": {
"limit value": "rate/duration"
},
"accept" : {
"limit value": "rate/duration"
} | "reject": {
"type": "reject type",
"limit value": "rate/duration"
} | "drop": {
"limit value": "rate/duration"
} | "mark": {
"set": "mark[/mask]",
"limit value": "rate/duration"
}
}19.2 Client Side Extension
The Firewalld Client Side Extension (CSE) accepts the rules specified by the SSE, and applies them using the firewalld command firewall-cmd. For example, new zones are added using the firewall-cmd --permanent --new-zone=work command. New firewall rules are added using the firewall-cmd --permanent --zone=work --add-rich-rule 'rule family=ipv4 source address=172.25.1.7 service name=ftp reject'.
Let’s check the Resultant Set of Policy on our Linux client.
> sudo /usr/sbin/samba-gpupdate --rsop
[sudo] password for root:
Resultant Set of Policy
Computer Policy
GPO: Default Domain Policy
=================================================================
CSE: gp_firewalld_ext
-----------------------------------------------------------
Policy Type: Rules
-----------------------------------------------------------
[
[ work ] =
[
[ rule ] =
[ family ] = ipv4
[ source address ] = 172.25.1.7
[ service name ] = ftp
[ reject ] =
]
]
-----------------------------------------------------------
Policy Type: Zones
-----------------------------------------------------------
[ work ]
-----------------------------------------------------------
-----------------------------------------------------------
=================================================================Let’s now force an apply, and verify that rule gets applied.
> sudo /usr/sbin/samba-gpupdate --force
> sudo tdbdump /var/lib/samba/gpo.tdb -k "TESTSYSDM$" \
| sed -r "s/\\\22/\"/g" | sed -r "s/\\\5C/\\\\/g" \
| xmllint --xpath "//gp_ext[@name='Security/Firewalld']" - \
| xmllint --format -
<gp_ext name="Security/Firewalld">
<attribute name="rule:work:f480...e3a8">
rule family=ipv4 source address=172.25.1.7
service name=ftp reject
</attribute>
</gp_ext>Unfortunately, at the time of this writing, firewall-cmd appears to be unable to list installed rich rules. We can verify that our rule has applied though by trying to apply it again.
> sudo firewall-cmd --permanent --zone=work --add-rich-rule \
'rule family=ipv4 source address=172.25.1.7
service name=ftp reject'
Warning: ALREADY_ENABLED: rule family=ipv4
source address=172.25.1.7 service name=ftp reject
successAttempting to add the rule, we can see that firewalld warns us that the rule is already enabled.