6 Password and Kerberos Policies

The purpose of these policies is to enforce password complexity and kerberos rules on a Samba Active Directory Domain Controller (ADDC). When a Linux client is not an ADDC, these policies are disabled and ignored automatically.
These policies are physically stored on the SYSVOL in the MACHINE/Microsoft */Windows NT/SecEdit/GptTmpl.inf** file in the subdirectory of the Group Policy Object. They are stored in ini format, and are easily modified manually using a text editor.
6.1 Server Side Extension
The Group Policy Management Editor (GPME) contains a built in Server Side Extension for Password and Kerberos Policies. There is also a samba-tool command to modify these policies.
6.1.1 Managing Password and Kerberos Policies via the GPME
Open the GPME and navigate to Computer Configuration > Policies > Windows Settings > Security Settings > Account Policy.
6.1.1.1 Password Policies
The following password policies are applicable to a Samba ADDC:
- Maximum password age
- Minimum password age
- Minimum password length
- Password must meet complexity requirements
To set password policy settings using the Group Policy Management Editor (GPME), follow these steps:
Open the Group Policy Management Editor (GPME). For instructions on accessing the GPME, see chapter 4 section 4.1.
In the left pane of the GPME, navigate to Computer Configuration > Policies > Windows Settings > Security Settings > Account Policy > Password Policy.
In the right pane, double-click the “Maximum password age” policy.
In the “Maximum password age” dialog box, click the Enabled option and enter 42 in the “Value” field.
Click OK to close the “Maximum password age” dialog box.
In the right pane, double-click the “Minimum password age” policy.
In the “Minimum password age” dialog box, click the Enabled option and enter 1 in the “Value” field.
Click OK to close the “Minimum password age” dialog box.
In the right pane, double-click the “Minimum password length” policy.
In the “Minimum password length” dialog box, click the Enabled option and enter 7 in the “Value” field.
Click OK to close the “Minimum password length” dialog box.
In the right pane, double-click the “Password must meet complexity requirements” policy.
In the “Password must meet complexity requirements” dialog box, click the Enabled option.
Click OK to close the “Password must meet complexity requirements” dialog box.
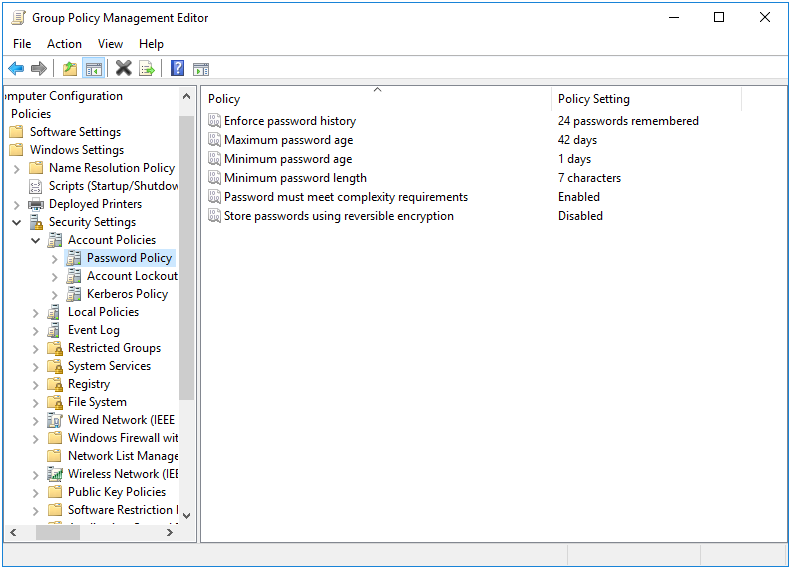
Figure 6.1: Password Policies
6.1.1.2 Kerberos Policies
The following Kerberos policies are applicable to a Samba ADDC:
- Maximum lifetime for service ticket
- Maximum lifetime for user ticket
- Maximum lifetime for user ticket renewal
To set Kerberos policy settings, follow these steps:
In the left pane of the GPME, navigate to
Computer Configuration > Policies > Windows Settings > Security Settings > Account Policy > Kerberos Policy.In the right pane, double-click the “Maximum lifetime for service ticket” policy.
In the “Maximum lifetime for service ticket” dialog box, click the Enabled option and enter 600 in the “Value” field.
Click OK to close the “Maximum lifetime for service ticket” dialog box.
In the right pane, double-click the “Maximum lifetime for user ticket” policy.
In the “Maximum lifetime for user ticket” dialog box, click the Enabled option and enter 10 in the “Value” field.
Click OK to close the “Maximum lifetime for user ticket” dialog box.
In the right pane, double-click the “Maximum lifetime for user ticket renewal” policy.
In the “Maximum lifetime for user ticket renewal” dialog box, click the Enabled option and enter 7 in the “Value” field.
Click OK to close the “Maximum lifetime for user ticket renewal” dialog box.
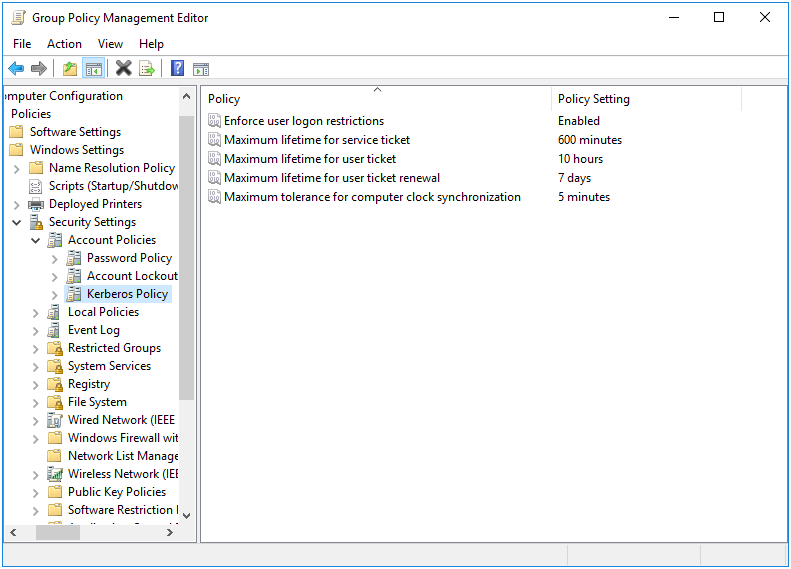
Figure 6.2: Kerberos Policies
6.1.2 Managing Password and Kerberos Policies via samba-tool
The Password and Kerberos policies can also be set via samba-tool gpo manage security set <gpo> <setting> <value>.
The command accepts the following parameters:
<gpo>: The name of the GPO that you want to modify.<setting>: The name of the smb.conf setting that you want to set.<value>: The value that you want to set for the specified setting.
The setting parameter must be one of the following:
| Setting | Description |
|---|---|
| MaxTicketAge | Maximum lifetime for user ticket |
| MaxServiceAge | Maximum lifetime for service ticket |
| MaxRenewAge | Maximum lifetime for user ticket renewal |
| MinimumPasswordAge | Minimum password age |
| MaximumPasswordAge | Maximum password age |
| MinimumPasswordLength | Minimum password length |
| PasswordComplexity | Password must meet complexity requirements |
6.2 Client Side Extension
The Password and Kerberos policies are separated into two Client Side Extensions (CSE), gp_access_ext and gp_krb_ext. The Password policies (internally known as System Access) apply password complexity rules directly to the ADDC SamDB in the applicable LDAP attributes. The Kerberos policies are stored in our Group Policy Cache, and are fetched directly by the samba daemon when it loads.
In the previous section we saw that our Password and Kerberos policies were already initialized to some defaults. If we now go to our Linux client, and check the Resultant Set of Policy, we see this:
> sudo /usr/sbin/samba-gpupdate --rsop
Resultant Set of Policy
Computer Policy
GPO: Default Domain Policy
=================================================================
CSE: gp_access_ext
-----------------------------------------------------------
Policy Type: System Access
-----------------------------------------------------------
[ MinimumPasswordAge ] = 1
[ MaximumPasswordAge ] = 42
[ MinimumPasswordLength ] = 7
[ PasswordComplexity ] = 1
-----------------------------------------------------------
-----------------------------------------------------------
CSE: gp_krb_ext
-----------------------------------------------------------
Policy Type: Kerberos Policy
-----------------------------------------------------------
[ MaxTicketAge ] = 10
[ MaxRenewAge ] = 7
[ MaxServiceAge ] = 600
-----------------------------------------------------------
-----------------------------------------------------------
=================================================================Remember that these policies will only be listed if your Linux client is a Samba ADDC.
Let’s now force a policy apply, and check that the settings have changed.
> sudo /usr/sbin/samba-gpupdate --force
> sudo tdbdump /var/lib/samba/gpo.tdb -k "TESTSYSDM$" \
| sed -r "s/\\\22/\"/g" | sed -r "s/\\\5C/\\\\/g" \
| xmllint --xpath "//gp_ext[@name='System Access' or
@name='Kerberos Policy']" -
<gp_ext name="System Access">
<attribute name="minPwdAge"/>
<attribute name="maxPwdAge"/>
<attribute name="minPwdLength"/>
<attribute name="pwdProperties"/>
</gp_ext>
<gp_ext name="Kerberos Policy">
<attribute name="kdc:user_ticket_lifetime"/>
<attribute name="kdc:renewal_lifetime"/>
<attribute name="kdc:service_ticket_lifetime"/>
</gp_ext>
> sudo tdbdump /var/lib/samba/gpo.tdb \
-k 'kdc:user_ticket_lifetime'; echo
10
> sudo tdbdump /var/lib/samba/gpo.tdb \
-k 'kdc:service_ticket_lifetime'; echo
10
> sudo tdbdump /var/lib/samba/gpo.tdb \
-k 'kdc:renewal_lifetime'; echo
168You can see the Kerberos policies are all stored in their own keys in the Group Policy Cache (/var/lib/samba/gpo.tdb), and they are all stored in hours. On the SYSVOL, they are actually stored in hours, minutes, and days, respectively. The reason these are all stored in hours on the system is that the samba daemon expects these attributes in hours.
If we check the contents of the GptTmpl.inf and do some conversion, we can confirm these are correct.
>>> from samba.gp.gp_sec_ext import mins_to_hours, days_to_hours
>>> MaxTicketAge = 10
>>> MaxServiceAge = 600
>>> MaxRenewAge = 7
>>> mins_to_hours(MaxServiceAge)
'10'
>>> days_to_hours(MaxRenewAge)
'168'It also helps to know how these Kerberos policies map to the samba daemon settings.
| Kerberos.Policy | Samba.Setting | Conversion |
|---|---|---|
| MaxTicketAge | kdc:user_ticket_lifetime | None |
| MaxServiceAge | kdc:service_ticket_lifetime | Minutes to Hours |
| MaxRenewAge | kdc:renewal_lifetime | Days to Hours |
While the Kerberos policies have been stored to the Group Policy Log as expected, let’s next verify that the Password policies have been applied using the following ldapsearch.
> ldapsearch -H ldap://lizardo.suse.de -x -W \
-D "Administrator@lizardo.suse.de" \
-b DC=lizardo,DC=suse,DC=de \
-s base minPwdAge maxPwdAge minPwdLength pwdProperties
# lizardo.suse.de
dn: DC=lizardo,DC=suse,DC=de
maxPwdAge: -36288000000000
minPwdAge: -864000000000
minPwdLength: 7
pwdProperties: 1We can confirm these were set correctly by checking the contents of the GptTmpl.inf, plus doing some type conversion.
[System Access]
MinimumPasswordAge = 1
MaximumPasswordAge = 42
MinimumPasswordLength = 7
PasswordComplexity = 1>>> from samba.gp.gp_sec_ext import days2rel_nttime
>>> MinimumPasswordAge = 1
>>> MaximumPasswordAge = 42
>>> MinimumPasswordLength = 7
>>> PasswordComplexity = 1
>>> days2rel_nttime(MaximumPasswordAge)
'-36288000000000'
>>> days2rel_nttime(MinimumPasswordAge)
'-864000000000'Finally, here is how these policies map.
| Password.Policy | LDAP.Attribute | Conversion |
|---|---|---|
| MinimumPasswordAge | minPwdAge | Days to NTTIME |
| MaximumPasswordAge | maxPwdAge | Days to NTTIME |
| MinimumPasswordLength | minPwdLength | None |
| PasswordComplexity | pwdProperties | None |